Sessions in PHP is a best way to store information across various pages. They help us to store information of a user on a server unlike cookies which store user info on clients computer. This tutorial is about PHP session hijacking and its prevention.
Let’s dive into more detail.
All of us visit Facebook, do upload posts and then log out. Everything here works like a chain, one gets connected to another and share information.
But the question here arises is how this works and how the server knows that it is you?
Everything on internet works on HTTP address and it is stateless. It means it can change anytime. How server will know it is you?
Sessions come into play and help us to get out from this problem. They store user information and we use them across multiple pages to validate the user.
Often, Sessions store precious user information like credit cards, login info or any other information. So we have to take every step to make it safer.
Now we have a basic understanding of Sessions let’s look at Session hijacking.
PHP Session Hijacking
The most important part of a session is ‘SESSION ID’. We have to protect it from every angle. If it gets into the hand of a bad guy, the user is no longer safe.
To get short answer of session hijacking is illustrated in below image.
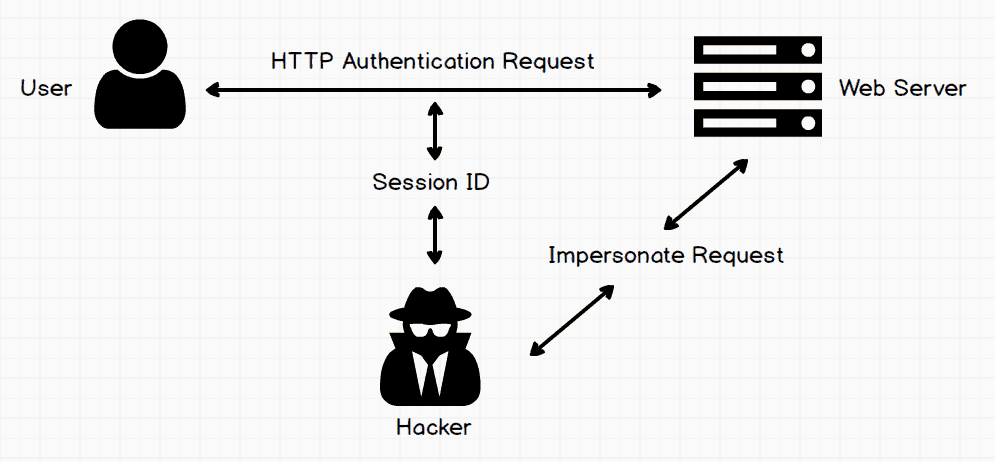
Many of you with eagle eyes wouldn’t have understood what it is. Let me explain it in easy and lucid English.
When the user sends an HTTP request, the hacker stoles the session ID and uses that ID to get access as a legal user.
Hackers can use many ways to do it. For Example, attacker can gain the valid session ID by running malicious code or program at client side. Another way is to use a session sniffer method to access valid session.
All of us know, no one is 100% secure even the giant Google. But someone has rightly said,
Prevention is better than cure.
You should have good programming habits. You can read my article on:
Best Programming Habits every Developer Must Have
We must (not should) secure the code from the first line. There are many ways of abusing sessions like Session Hijacking and Session Fixation.
Here I am focusing only on Session Hijacking. You can read more about session Fixation on my article:
Session Fixation and How To Prevent It
Ways of Session Hijacking
There are many ways to do Session hijacking and the most hijacking methods which the hacker uses are given below.
Network Traffic
The easiest and simplest method of hijacking a session is Network Traffic. If the attacker successfully entered the traffic, he will get the gold easily. This type of abuse is possible when using wi-fi because wi-fi is sniff-able.
You can prevent from this attack easily by using wired connections.
Session ID Exposure
PHP appends a session ID to relative URL’s, so making it easier to hijack.
But you can prevent from this attack by setting few directives in php.ini file.
Search this directive in php.ini file and check whether it is off or not.
session.use_trans_sid
By default it is set to off and leave it if it is off.
Forwarding
Bad guys can easily trick users through emails. They can send the links to emails by offering discount or any other thing. The link may be corrupted and the user will get abused by the bad guys.
We discussed all the stuff which is about session hijacking in PHP. Now let’s see how we can prevent it.
How To Prevent Session Hijacking in PHP?
You have now a full concept of session hijacking like what it is and how it is done? But until now I haven’t told you how to take every measure to prevent from it.
Believe me, these recommendations wouldn’t make your code 100% secure but will make it difficult for attacker to gain access.
Let me give you the recommendations to prevent from session hijacking in PHP.
Use SSL
This is the primary recommendation for preventing such attacks. It can make your website more secure. I will not get into detail, so use SSL.
You may heard that getting SSL is expensive. But not anymore, checkout my article on:
Getting Free SSL and How to Install it on your Server
Don’t Use $_GET Variable
Many times, the users accidentally reveal their Session_ID’s making it easier to get hijacked. But you can prevent this mistake by setting few directives in php.ini file.
ini_set( ‘session.use_only_cookies’, TRUE );
ini_set( ‘session.use_trans_sid’, FALSE );
The ini_set() function is used to override directives in the file.
Session Lifetime
Always set timeout for sessions. If you haven’t set timeout of your sessions, you are providing more time to the attacker to attack the sessions.
You can set timeout using this directive in php.ini file.
ini_set( ‘session.cookie_lifetime’, 1200 )
Here the time is in seconds (1200 = 20 minutes).
Regenerate Session ID’s
Always regenerate session id’s when the user refresh’s browser or changes status. You can do this by including this function in your php code not php.ini file. For example,
<?php
session_start();
$password= filter_input(INPUT_POST, 'password', FILTER_SANITIZE_STRING);
$result = $mysqli->query("SELECT * FROM users");
$user = $result->fetch_assoc();
if ( password_verify($password, $user['password']) ) {
session_regenerate_id(true);
}
Here i’m regenerating session id every time the user refresh or reload his/her browser.
Also I included a Boolean ‘true’ which commands PHP executor to delete the previous session id and generate new one.
If set blank or set to ‘false’, the old session id will also be recognised as valid session.My recommendation is set it to true every time.
The whole article focused on session hijacking and its prevention.
I hope you liked the article and if so then please do share it so it reaches to everyone and will get benefit from it.
It will be great if you have any suggestion or recommendation.

Leave a Reply